The Nicehash Hack 2017
You could probably write a whole book about the Nicehash hack – if you want to call it that – from 2017.
The reactions of the company owners immediately after the hack, the statements made about a refund to customers. We’re talking about losses of over 53 million euros and a company that had made a total profit of 3.46 million euros in the previous years according to its own annual reports.
The investigation carried out by an investigative firm and its report, in which North Korean hackers were held responsible for the first time. A report full of strange statements and allegations that were implausible for us from the outset. 1
Ultimately, an indictment and international arrest warrants were issued by the U.S. authorities against the aforementioned North Korean hackers and the Nicehash hack was mentioned in this indictment. With regard to this indictment, it should be mentioned briefly that the Nicehash hack is only briefly mentioned in it and that the indictment refers to many other cases, some of which are much more extensive. It is therefore quite possible that the U.S. authorities assumption was based on the previously mentioned report and not on their own investigations.
After the hack, both the then CEO and the company founder and then CTO of Nicehash resigned. The father of the company founder, a complete outsider who had no experience in the IT sector, let alone with cryptocurrencies, then took over the management of the company.
The background of the founder of Nicehash is also worth mentioning. He was finally convicted for his involvement in the “Mariposa Botnet” and served a prison sentence of several years. The “Mariposa Botnet” was a computer program for the illegal theft of credit cards and bank data, for example. The previous history of the company founder is a decisive factor in order to be able to classify our later assumption and statement on the possibly falsely laid traces and the investigations influenced / hindered by them.
The points outlined so far were only a very brief list of a few of the circumstances of this case. At this point, however, we will only really go into one fact in detail. This fact is of a purely technical nature and can therefore be clearly proven by us with our cryptoforensics resources.
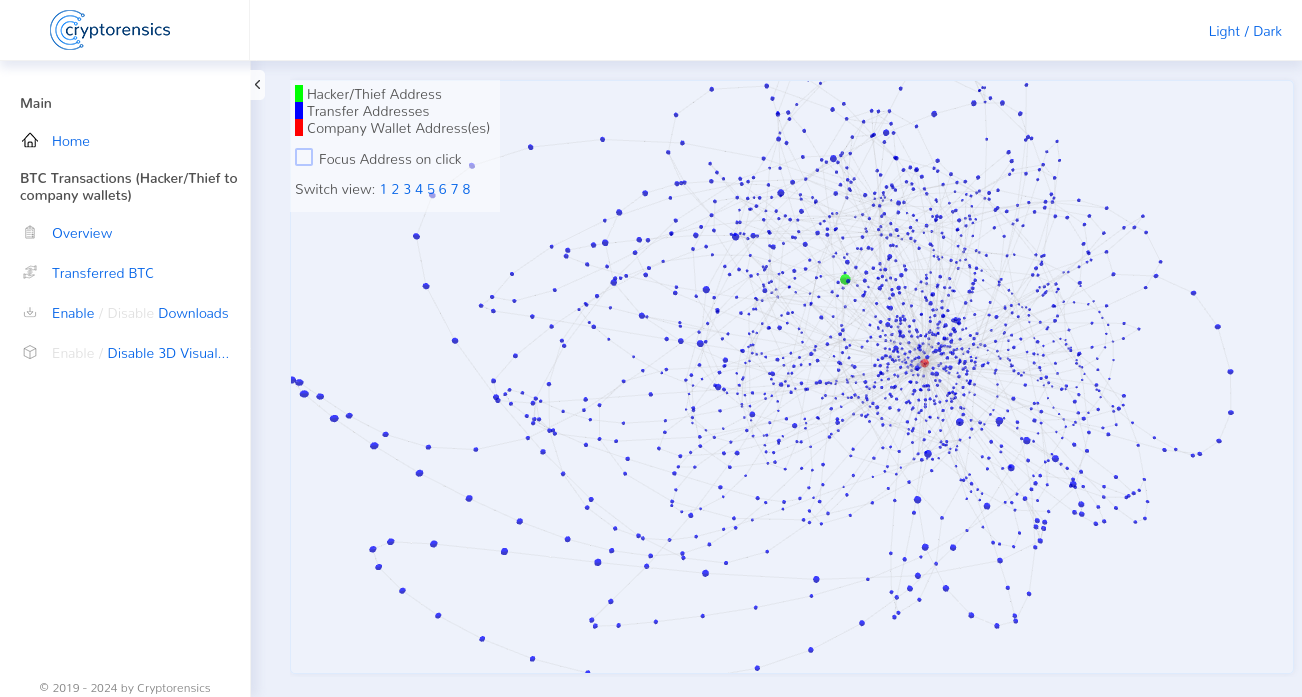
A theft by North Korean hackers never took place in the Nicehash case. The stolen Bitcoins, which were stolen by the hackers / thieves, initially ended up at the Bitcoin address 1EnJHhq8Jq8vDuZA5ahVh6H4t6jh1mB4rq. From there, the traces of the bitcoins were attempted to be covered by thousands of transactions. A mixer may have been used for this purpose, which may also have been used by the North Korean hackers. 2 After the attempt to conceal the whereabouts of the stolen Bitcoins, they were ultimately transferred back to a single Bitcoin wallet. And this Bitcoin wallet belonged to – Nicehash!
1 In our opinion, the investigation by the external company is not responsible for the untrustworthy statements, but in our opinion the deliberately false tracks laid by Nicehash.
2 We have not investigated this circumstance further, as it is ultimately irrelevant to our investigations and their outcome.
Date
December 2017
Damage amount
~4,700 BTC / ~53,815,000 EUR
Status
open
Analyzes
The first suspicious facts
Shortly after the theft of the ~4,700 BTC from Nicehash’s accounts – which, mind you, did not contain Nicehash’s assets, but the assets of Nicehash’s customers – the first suspicions of fraud by Nicehash itself emerged.
The then CEO and CTO of Nicehash published a statement in a video just one day after the hack. In this video, the two people report on the incidents of the previous day and the statements made in the video alone left us with the feeling that this video and the hack of the previous day had been planned for a long time.
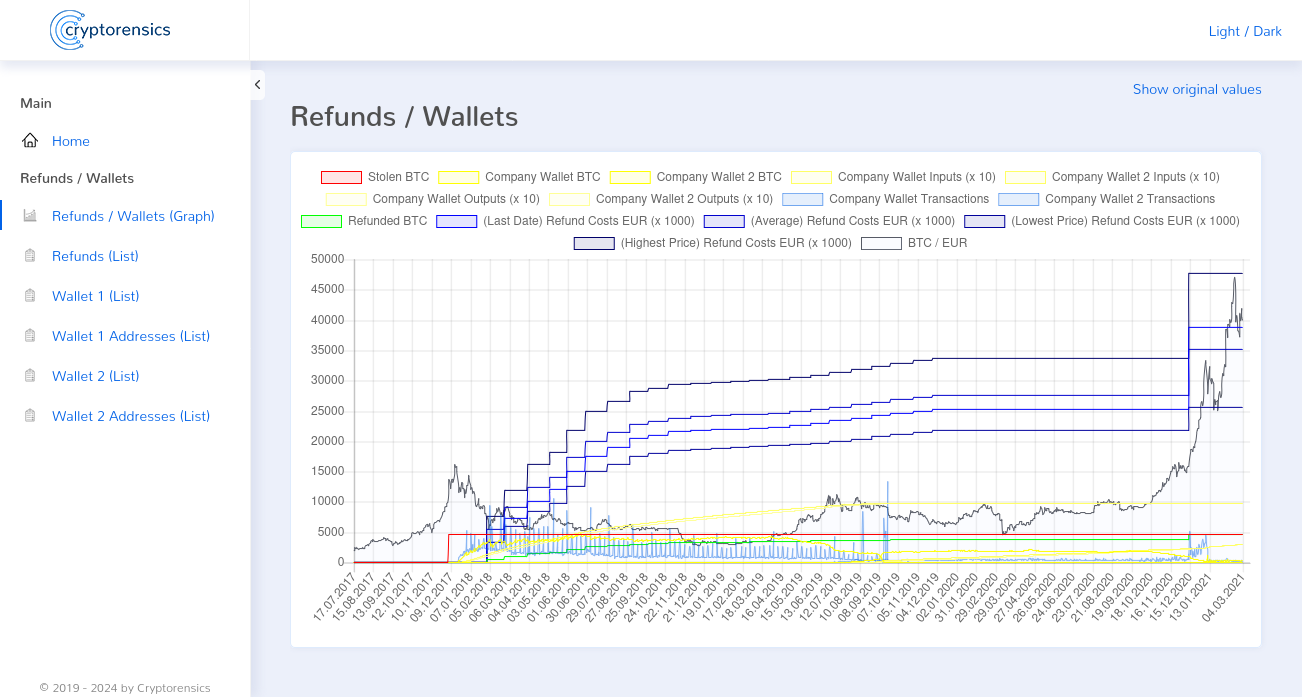
Shortly afterwards, on January 31, 2018, Nicehash announced in a press release that it would fully compensate its customers. This statement again seemed very suspicious to us. Especially as a Nicehash customer had also published an email shortly beforehand, which he had received from Nicehash, in which Nicehash had already announced the compensation of customers and named an unnamed investor as the funding for this. In the press release on the compensation of customers, however, there was no longer any mention of an investor and from this point on Nicehash claimed that the compensation would be financed from the company’s own profits. So now briefly to the profits of Nicehash. Nicehash’s corporate profits can be viewed in its publicly accessible annual reports. In 2015, Nicehash reported a profit of 77,750.00 euros, in 2016 a profit of 111,384.00 euros and in 2017, the year of the theft, a profit of 3,264,210.00 euros. The profits for the three years prior to the hack therefore amounted to a total of 3,460,344.00 euros. This figure compares to the value of the stolen ~4,700 BTC with a value of 37,858,500.00 euros on January 31, the day of the press release, and even 53,815,000.00 euros on the day of the theft.
A repayment would therefore have taken more than 10 years with the same profit as in 2017 if the Bitcoin price had not risen during these years. However, the repayments to customers were already completed in December 2020 and in December 2018, one year after the hack, 70% of the stolen bitcoins had already been repaid.
Further suspicions arose for us from the circumstances already briefly described, such as the company takeover by the father of the company founder, who was not from the industry, the statements on the alleged course of the hack by the CEO and CTO of Nicehash and, last but not least, the previous history of the company founder and CTO.
The analyses carried out
In order to be able to prove that Nicehash itself had committed fraud, we needed proof. All the suspicious facts described so far gave us a very clear picture, but they were just that – suspicious facts. We therefore carried out many analyses and investigations until we finally came to the solution of the case and the clear evidence.
These analyses and investigations included, but were not limited to, the following research:
- Tax data from publicly available annual reports of the company.
- Statements made by the company to its customers and the press (e.g. in its blog).
- Research on the presumed turnover of the company (through statistics on their website).
- Research into the background of the company founder (who has already been sentenced to several years in prison for computer fraud in another case).
- Extensive research into the refunds that the company made to its customers.
The breakthrough
The solution – and the subsequent clear proof of the fraud carried out by Nicehash itself – was found when we were able to locate the new company wallet that Nicehash used after the hack. Shortly after the hack, very large amounts of Bitcoin were received on this company wallet. We were unable to explain the extent of these deposits by Nicehash customers. On February 5, 2018, less than two months after the theft, there were already ~3,800 BTC on this wallet and on June 21, 2018, the total of the stolen ~4,700 BTC was finally exceeded by the wallet’s account balance. This naturally raises the crucial question of where these immense assets came from.
The final and decisive analysis
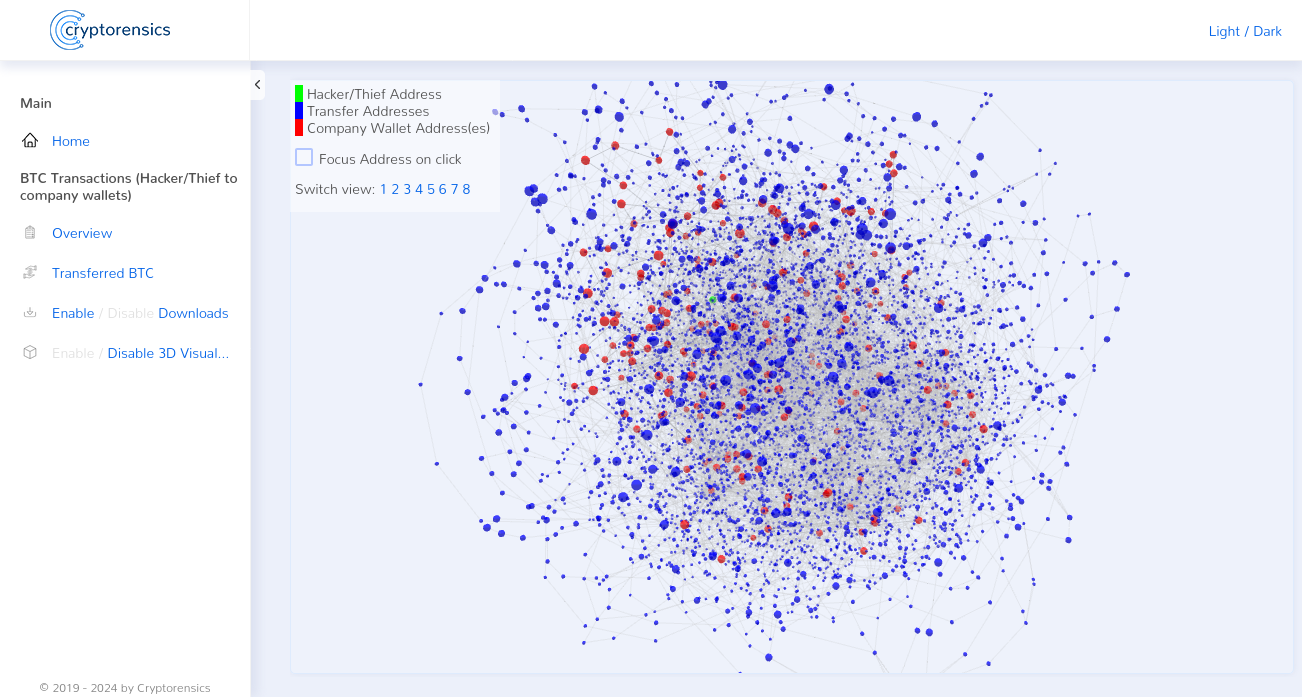
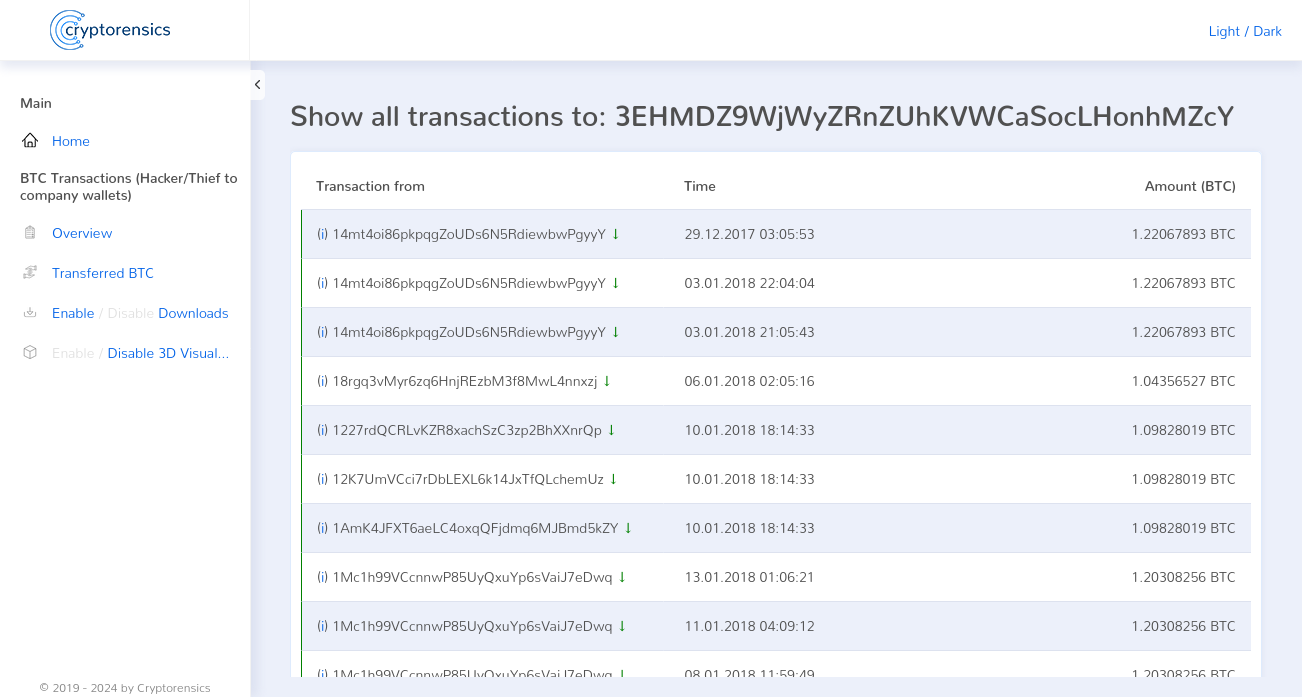
Since we had suspected for a long time that the fraud was carried out by Nicehash itself, the next step was obvious. In order to clearly prove that the fraud had been carried out, all we had to do was link the inputs on Nicehash’s new company wallet with the Bitcoin address that was used after the theft. To do this, we developed software that scanned all transactions starting from the address 1EnJHhq8Jq8vDuZA5ahVh6H4t6jh1mB4rq and ended the scan the moment the transactions ended on the new Nicehash company wallet.
Of course, one could assume that even in the case of theft by third parties, such as North Korean hackers, at least a small portion of the bitcoins could end up on the Nicehash wallet at some point.
Depending on the filters applied and the length of the transaction chains, our analysis was able to prove a clear receipt on the Nicehash wallet in the amount of ~1,115 BTC up to ~2,749 BTC, the origin of which was the Bitcoin address 1EnJHhq8Jq8vDuZA5ahVh6H4t6jh1mB4rq.
The bottom line
We have published this case under the title Insider Hack because we were able to clearly prove that the assets stolen from Nicehash’s customers were ultimately returned to Nicehash’s accounts. We can only explain this and all the other circumstances mentioned with an insider hack and a subsequent concealment of the same.
The data
Here you can find the Demo of analyzes data and the Manual for the analysis data (.pdf)