The Hashflare case
We have chosen the Hashflare fraud case for publication here because it is an example for many fraud cases that use the same principle. The so-called cloud mining. This involves selling computing power to customers that is used for mining cryptocurrencies. In the case of fraud, however, this computing power is not available, or not available to the extent that it is sold, and the profits allegedly generated are financed by the deposits of other customers. This is therefore a classic Ponzi or pyramid scheme.
Unfortunately, cryptocurrencies are perfect for this, as unlike a rented web server in the cloud, for example, it is difficult for a layperson to verify the actual existence of the rented computing power. Proof of an underlying Ponzi scheme, i.e. the distribution of profits to customers from the deposits of other customers and the absence of Coinbase transactions 1, on the other hand, is quite easy to prove using crypto forensics.
The operators of Hasflare.io had already committed another fraud before the cloud mining scam by selling alleged mining hardware that was never delivered, and then by founding an alleged crypto bank in which investor funds were embezzled. In our case description, however, we focus exclusively on the cloud mining scam committed on the Hashflare.io website, as we were able to analyze it in detail using our crypto forensics resources.
1 When a miner finds / generates a new Bitcoin block, they receive a reward in the form of new Bitcoins. This reward is paid out to the miner by means of so-called Coinbase transactions.
Date
2015 – 2018
Damage amount
~42,000 BTC
(of which ~ 21,000 BTC paid back to customers)
Status
open
Analyzes
The first moments of suspicion
Cloud mining of cryptocurrencies should actually be viewed as suspicious from the outset. For the very simple reason that it does not actually make economic sense for a miner to rent its computing power to customers. Unlike providers of web servers, for example, which are only economically viable for the operator if they are rented out to customers, the hardware for cryptomining generates its profits through cryptomining. Interposing a customer to whom this computing power is rented therefore makes no economic sense if you really make a profit from mining. And this is precisely what the providers of cloud mining claim, that they operate profitable cryptomining.
Hashflare’s referral program could also be seen as a further cause for suspicion. Hashflare customers were promised very high percentages of their deposits if they acquired additional customers. Even if there are referral programs that are used for serious business models, it should always be viewed critically if the percentage shares are very high. Hashflare has offered a commission of 10% for its referral program.
And ultimately, as is the case with all Ponzi schemes, at some point the operators have to end the business because there are no longer enough deposits from customers to finance the payouts of the alleged profits. Hashflare reached this point in early 2018. Hashflare then simply canceled all existing mining contracts. The payments already made for these contracts were simply withheld / embezzled. Hashflare justified this action by stating that mining was no longer profitable and referred to its general terms and conditions, which provide for the automatic cancellation of contracts in the event of mining becoming unprofitable for 14 consecutive days.
For a customer who had concluded a new contract at the beginning of 2018, this meant a virtual total loss.
The first investigations
Hashflare was registered as a letterbox company in Scotland. The perpetrators of the fraud could not be traced via this registration.
However, there was a reference on the Hashflare.io website to the company Hashcoins.com, which was listed there as the operator of Hashflare. Hashcoins.com is the company mentioned at the beginning, which sold mining hardware that was never delivered. An archived version of the Hashcoins.com website finally listed the creators of Hashcoins.com and thus also of Hashflare.io.
The creators of the Scottish shell company and operators of Hashflare.io were from Estonia.
Proof of the fraud
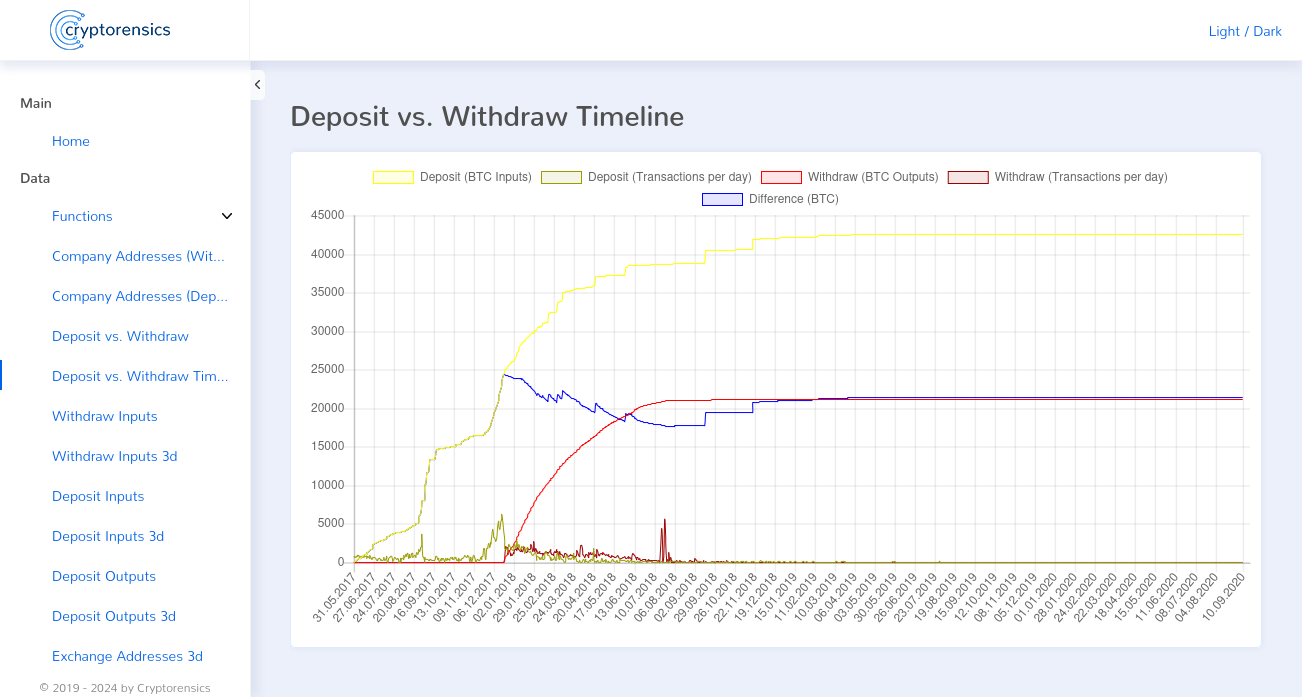
Now that we knew the perpetrators of the fraud, the next step was to analyze the Bitcoin transactions to determine the approximate extent of the fraud and to prove the fraud. In this case, we were only able to determine the approximate extent, as Hashflare customers also had the option of concluding mining contracts, in addition to paying with cryptocurrencies, via bank transfer and credit card payments. Our crypto forensics capabilities are limited to analyzing crypto transactions, so there was a dark figure regarding bank and credit card payments.
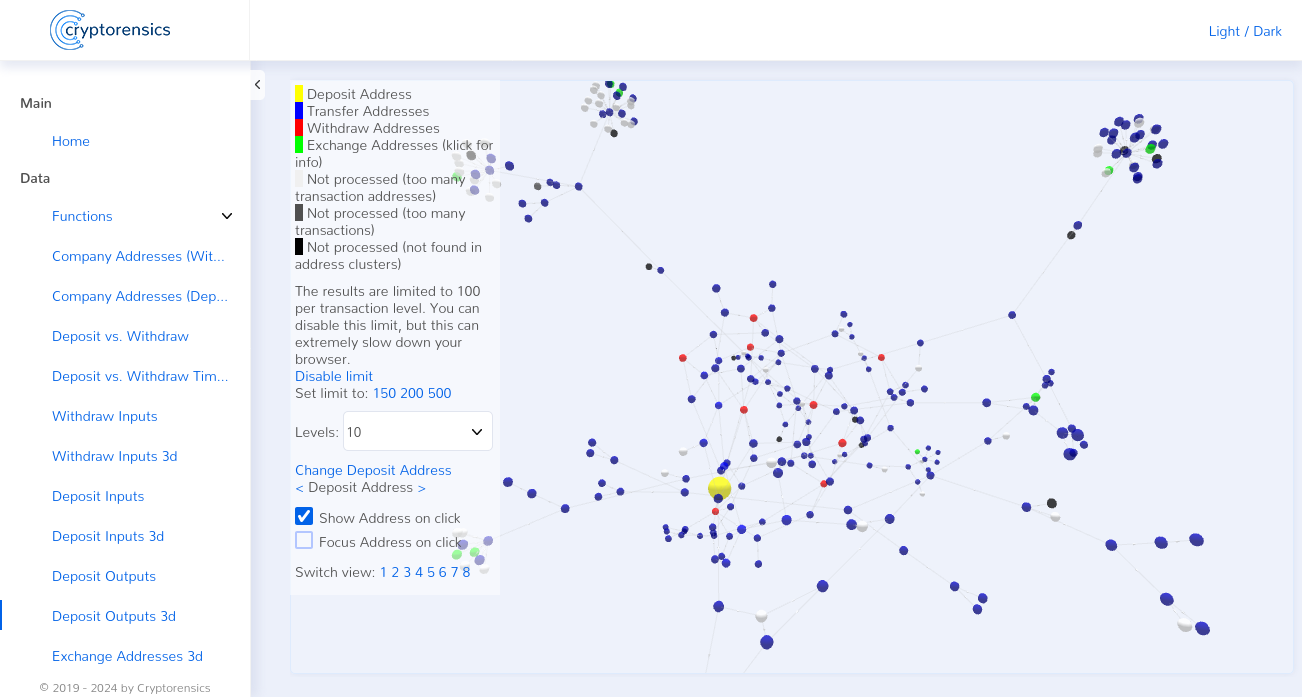
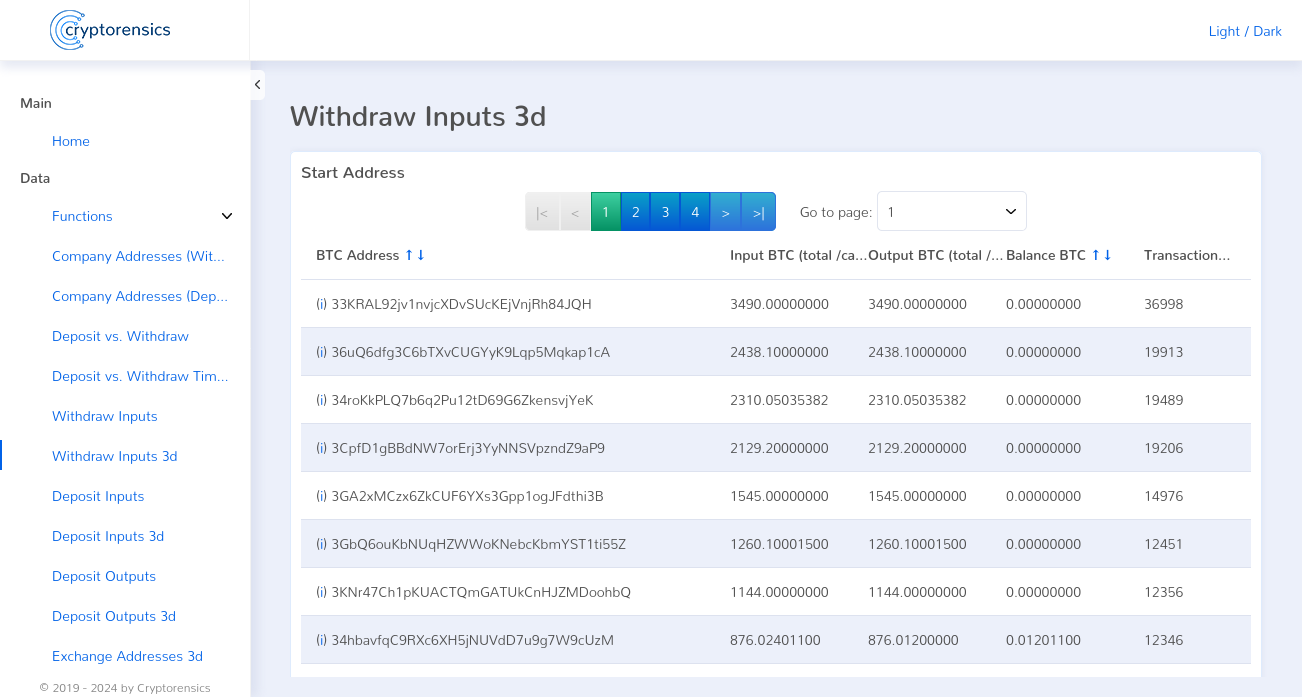
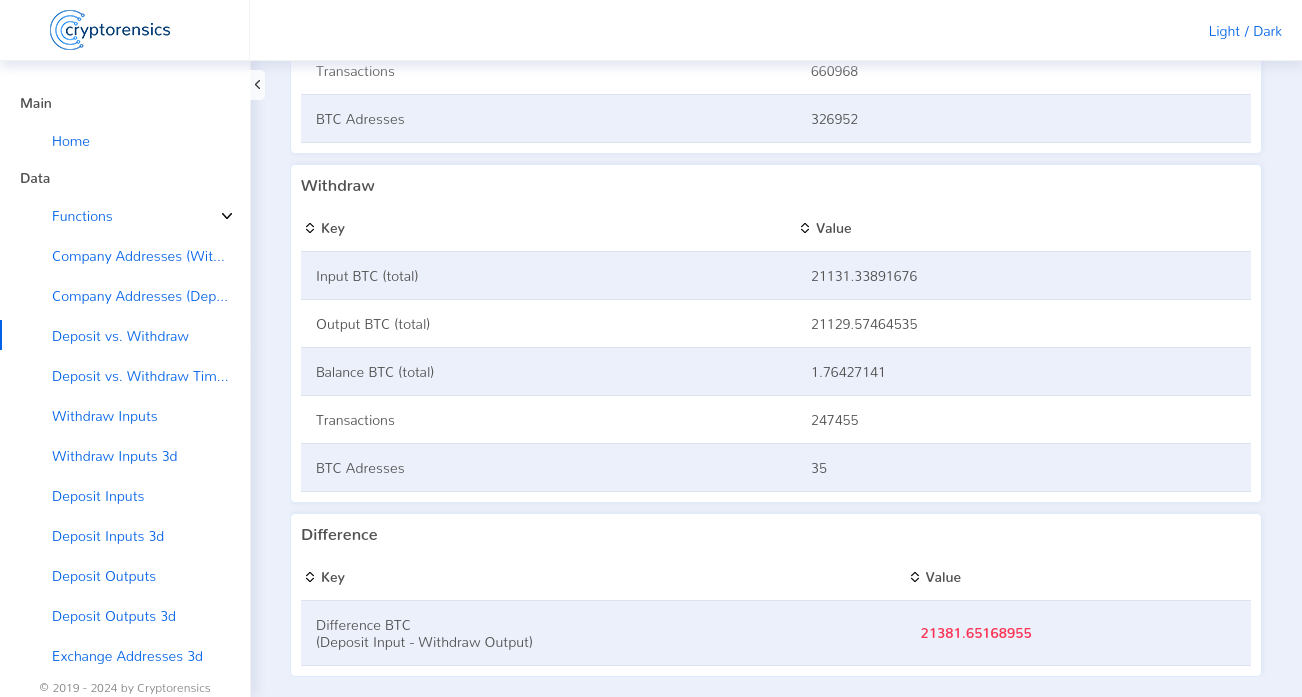
In the first step of the following investigations, we focused on the deposits made by customers and the payouts made. To this end, we tracked down all of Hashflare’s deposit addresses. These were over 300,000 Bitcoin addresses. We also identified all payout addresses. These were only 35 Bitcoin addresses. The comparison of deposits and withdrawals showed a difference of ~21,000 Bitcoin.
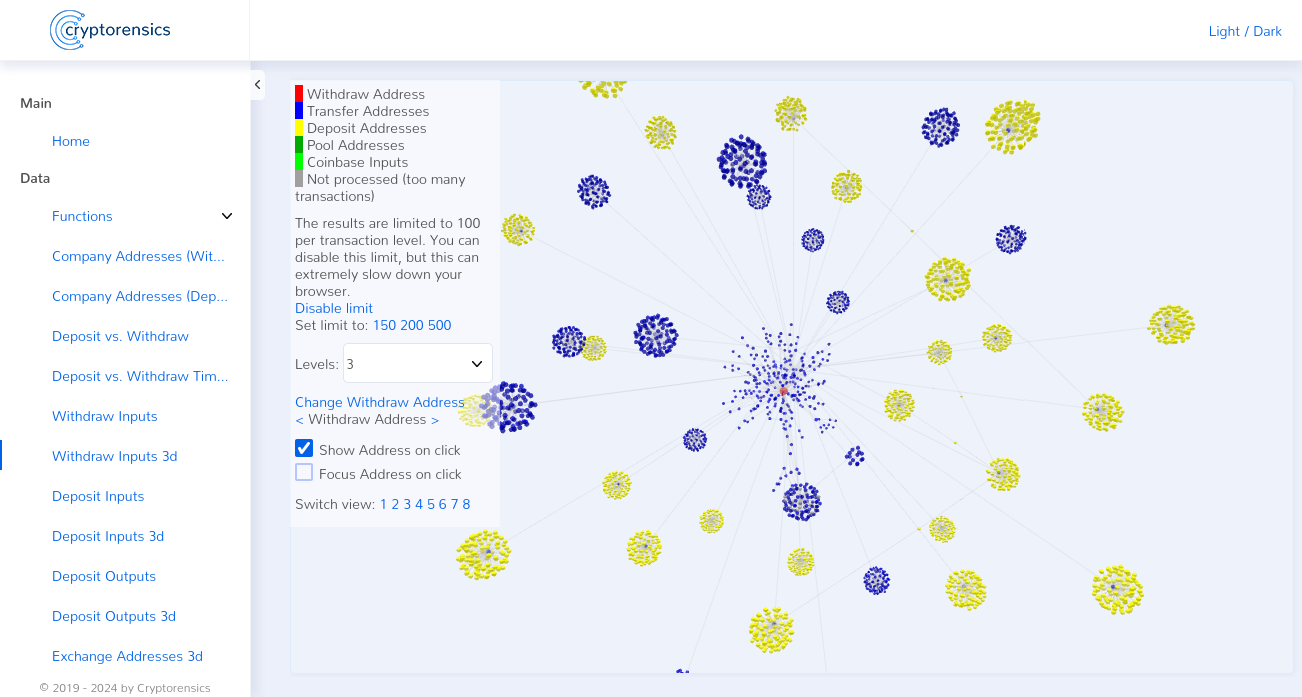
In the next step, we provided proof that no Bitcoin mining had ever taken place. Hashflare allegedly operated the Bitcoin mining via 5 different mining pools. We therefore identified all Bitcoin addresses of these mining pools. This resulted in ~280,000 individual Bitcoin addresses. Next, we analyzed how many deposits Hashflare received from the mining pool addresses. These were negligible amounts, which could be explained by the fact that Hashflare’s customers invested their profits generated from these mining pools into Hashflare. In order to provide definitive proof that no Bitcoin mining had taken place, we examined all inputs for Coinbase transactions 1. We were only able to find the aforementioned Coinbase transactions in the same small number as the deposits from the pool addresses. These were therefore also attributable to Hashflare customers.
In the final step, we proved that the payouts to customers were all attributable to deposits by customers. A comparison of these deposits and withdrawals ultimately showed that Hashflare had misappropriated ~50% of all customer deposits. This was the ~21,000 Bitcoin mentioned above.
The bottom line
The size of the case described shows that cloud mining fraud is a very successful fraud model. We have also identified cases that took place before Hashflare and in some cases were even more extensive than Hashflare.
Even though the perpetrators of Hashflare were ultimately charged and extradited to the USA, where they are currently awaiting trial, there is unfortunately no shortage of other cloud mining fraudsters.